A broad attack surface substantially amplifies an organization’s vulnerability to cyber threats. Allow’s understand with the instance.
The main element distinction between a cybersecurity menace and an attack is the fact a danger may lead to an attack, which could lead to harm, but an attack is an precise destructive function. The main distinction between the two is usually that a danger is opportunity, when an attack is true.
When implemented diligently, these procedures appreciably shrink the attack surface, making a more resilient security posture against evolving cyber threats.
A hanging Actual physical attack surface breach unfolded in a significant-security info center. Thieves exploiting lax physical security actions impersonated servicing workers and obtained unfettered use of the power.
It’s crucial to Take note which the Business’s attack surface will evolve over time as products are continuously included, new users are released and business demands modify.
Insider threats come from individuals within just a company who possibly unintentionally or maliciously compromise security. These threats may perhaps arise from disgruntled staff or People with entry to sensitive data.
Take away impractical features. Eliminating avoidable characteristics cuts down the volume of likely attack surfaces.
Use robust authentication guidelines. Take into consideration layering sturdy authentication atop your entry protocols. Use attribute-based mostly obtain Management or function-centered access obtain Handle to be certain details can be accessed by the best people.
For illustration, a company migrating to cloud solutions expands its attack surface to incorporate likely misconfigurations in cloud settings. A corporation adopting IoT products in a production plant introduces new components-based mostly vulnerabilities.
Use community segmentation. Applications such as firewalls and strategies including microsegmentation can divide the community into smaller sized units.
Electronic attacks are executed by interactions with digital programs or networks. The electronic attack surface refers to the collective electronic entry points and interfaces through which menace actors can attain unauthorized accessibility or trigger harm, for instance network ports, cloud providers, remote desktop protocols, purposes, databases and third-occasion interfaces.
Phishing ripoffs stick out as a widespread attack vector, tricking buyers into divulging sensitive details by mimicking genuine conversation channels.
Malware could possibly be installed by an attacker who gains usage of the community, but generally, men and women unwittingly deploy malware on their units or company community following clicking on a bad backlink or downloading an infected attachment.
This calls for continual visibility throughout all belongings, such as the Firm’s internal networks, their existence outdoors the firewall and an awareness of your programs and Cyber Security entities end users and programs are interacting with.
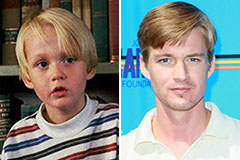 Mason Gamble Then & Now!
Mason Gamble Then & Now! Michelle Pfeiffer Then & Now!
Michelle Pfeiffer Then & Now! Freddie Prinze Jr. Then & Now!
Freddie Prinze Jr. Then & Now! Loni Anderson Then & Now!
Loni Anderson Then & Now! Bill Murray Then & Now!
Bill Murray Then & Now!